Web Security Tools
SANS Institute CIS Critical Security Controls. The CIS Critical Security Controls for Effective Cyber Defense. Domain name search tool that allows a wildcard search, monitoring of WHOIS record changes and history caching, as well as Reverse IP queries. Discover all Revlon cosmetics for eyes, lips, and face. Find haircolor, nail products, and beauty tools in one place. Check out our free tools, apps, and trials. Weve got you covered with free antiransomware, antivirus resources and many other free tools. The CIS Critical Security Controls are a recommended set of actions for cyber defense that provide specific and actionable ways to stop todays most pervasive and dangerous attacks. A principal benefit of the Controls is that they prioritize and focus a smaller number of actions with high pay off results. The Controls are effective because they are derived from the most common attack patterns highlighted in the leading threat reports and vetted across a very broad community of government and industry practitioners. They were created by the people who know how attacks work NSA Red and Blue teams, the US Department of Energy nuclear energy labs, law enforcement organizations and some of the nations top forensics and incident response organizations to answer the question, what do we need to do to stop known attacks. That group of experts reached consensus and today we have the most current Controls. The key to the continued value is that the Controls are updated based on new attacks that are identified and analyzed by groups from Verizon to Symantec so the Controls can stop or mitigate those attacks. Windows Vista Wii Theme. The Controls take the best in class threat data and transform it into actionable guidance to improve individual and collective security in cyberspace. Websecurify free and premium security tools automatically scan websites for vulnerabilities like SQL Injection, Crosssite Scripting and others. Too often in cybersecurity, it seems the bad guys are better organized and collaborate more closely than the good guys. The Controls provide a means to turn that around. SANS Supports the CIS Critical Security Controls with Training, Research and What Works. To support information security practitioners and managers implement the CIS Critical Security Controls, SANS provide a number of resources and information security courses. Sana Nuestra Tierra Para Descargar there. Critical Security Controls Courses. Security Operations Center Courses. Information Security Resources. Removal Tools. Use FSecures free utility tools to handle special tasks such as manually updating product databases, booting an unresponsive PC and removing specific. CIS Critical Security Controls Version 6. The SANS What Works program highlights success stories in cybersecurity real examples of how real security teams have made measurable improvements in the effectiveness and efficiency of their security controls. While most of the press coverage focuses on breaches and other security failures, there are thousands of cybersecurity leaders quietly working hard and make advances against threats while enabling business and mission needs. SANS expert John Pescatore interviews the end user and decision maker and produces a Q A formatted case study and a live webcast that allows security practitioners to take advantage of lessons learned and accelerate their own cybersecurity improvements. Check out recent SANS What. Works case studies Case Studies. Title. Vendor. Date. Web Security Tools' title='Web Security Tools' />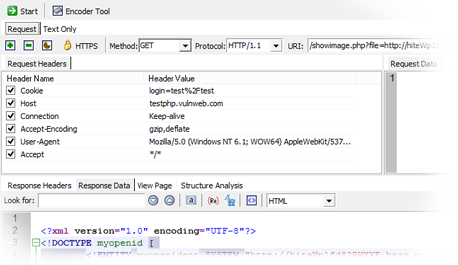 A Credit Union Increased Network Security With Network Access Control Based on Great Bay Software Beacon. Great Bay Software. August 4, 2. 01. 6What Works in Threat Prevention Detecting and Stopping Attacks More Accurately and Quickly with Threat. Security. Lets face it. Software has holes. And hackers love to exploit them. New vulnerabilities appear almost daily. If you have software we all do you need to. Get reliable, lowcost dialup Internet service, highspeed broadband Internet access, Web hosting more. Connect with us for savings, support satisfaction Our Hybrid Cloud Security solution protects physical, virtual, and cloud environments with the most complete set of security capabilities. Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers. PC Tools PC software is highly trusted, awardwinning performance utilities software for Windows, including Performance Toolkit, Registry Mechanic and File Recover. STOPThreat. STOPMay 1. Inspecting Encrypted Traffic with the Blue Coat SSL Visibility Appliance. Blue Coat. Mar. 2. What Works in Supply Chain and Partner Security Using Bit. Sight to Assess and Monitor Third Party Cybersecurity. Bit. Sight. Nov. 7, 2. Using White. Hat Sentinel. Dynamic and Static Solutions to Increase Application Security Before and After Production Deployment. White. Hat Security. Oct. 9, 2. 01. 5Lifecycle Vulnerability Management and Continuous Monitoring with Rapid. Nexpose. Rapid. 7Sept. Using Palo Alto Networks Next Generation Firewalls to Increase Visibility into Threats and Reduce Threat Risks. Palo Alto Networks. May 1. 9, 2. 01. 5Blocking Complex Malware Threats at Boston Financial. Invincea. Mar. 2. Increasing Security and Reducing Costs by Managing Administrator Rights with Process based Privilege Management. Viewfinity. Mar. 2. Reaping the Benefits of Continuous Monitoring and Mitigation at Pioneer Investments. Fore. Scout. Mar. How VCU uses Fire. Eye for Advanced Threat Detection and Prevention. Fire. Eye. Mar. 1. Adobe Audition 3 With Crack Torrent here. Increasing Vulnerability Management Effectiveness While Reducing Cost. Tenable. Feb. 1. 9, 2.
A Credit Union Increased Network Security With Network Access Control Based on Great Bay Software Beacon. Great Bay Software. August 4, 2. 01. 6What Works in Threat Prevention Detecting and Stopping Attacks More Accurately and Quickly with Threat. Security. Lets face it. Software has holes. And hackers love to exploit them. New vulnerabilities appear almost daily. If you have software we all do you need to. Get reliable, lowcost dialup Internet service, highspeed broadband Internet access, Web hosting more. Connect with us for savings, support satisfaction Our Hybrid Cloud Security solution protects physical, virtual, and cloud environments with the most complete set of security capabilities. Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers. PC Tools PC software is highly trusted, awardwinning performance utilities software for Windows, including Performance Toolkit, Registry Mechanic and File Recover. STOPThreat. STOPMay 1. Inspecting Encrypted Traffic with the Blue Coat SSL Visibility Appliance. Blue Coat. Mar. 2. What Works in Supply Chain and Partner Security Using Bit. Sight to Assess and Monitor Third Party Cybersecurity. Bit. Sight. Nov. 7, 2. Using White. Hat Sentinel. Dynamic and Static Solutions to Increase Application Security Before and After Production Deployment. White. Hat Security. Oct. 9, 2. 01. 5Lifecycle Vulnerability Management and Continuous Monitoring with Rapid. Nexpose. Rapid. 7Sept. Using Palo Alto Networks Next Generation Firewalls to Increase Visibility into Threats and Reduce Threat Risks. Palo Alto Networks. May 1. 9, 2. 01. 5Blocking Complex Malware Threats at Boston Financial. Invincea. Mar. 2. Increasing Security and Reducing Costs by Managing Administrator Rights with Process based Privilege Management. Viewfinity. Mar. 2. Reaping the Benefits of Continuous Monitoring and Mitigation at Pioneer Investments. Fore. Scout. Mar. How VCU uses Fire. Eye for Advanced Threat Detection and Prevention. Fire. Eye. Mar. 1. Adobe Audition 3 With Crack Torrent here. Increasing Vulnerability Management Effectiveness While Reducing Cost. Tenable. Feb. 1. 9, 2.